Black market selling hacked server access, Malaysia among top 10 countries affected
By Benjamin Cher June 16, 2016
- Kaspersky Lab exposes massive underground market selling hacked server access
- Market list over 70,000 servers across 173 countries, with Malaysia at No 10

KASPERSKY Lab researchers have exposed a massive underground market selling access to more than 70,000 hacked servers across 173 countries, with Malaysia within the top 10 and the most compromised in South-East Asia.
“It is all over the world, not just emerging countries – over 170 countries affected in different scales and proportions,” said Vitaly Kamluk, Asia Pacific director of Kaspersky Lab’s Global Research & Analysis Team (GREAT).
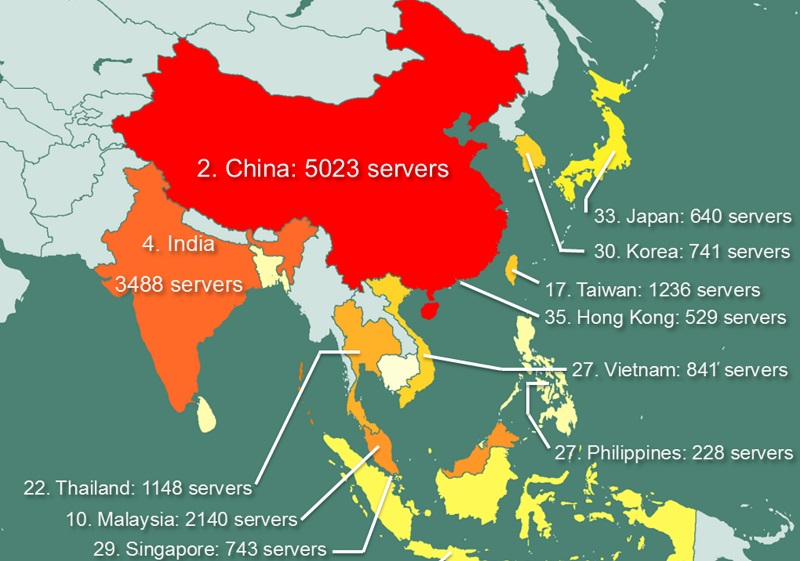
“Singapore for example, is in 29th place with 743 servers being offered – Malaysia has 2,140 servers (10th place) and Indonesia has 459 servers (37th place),” he told Digital News Asia (DNA) in a phone conversation.
The underground marketplace, dubbed xDedic and run by a Russian-speaking group, sells server information and login passwords that could be used to control these hacked servers.
The compromised machines were not only those owned by private or home users, but also included servers from “many different government networks, ISPs (Internet service providers), telcos, universities, medical institutions, and many more,” said Kamluk.
“This is something we have never seen before in terms of scale – it is a professional service developed over many years.
“Our research shows it has been operational since 2014, with tech support, a message board and training [for users].
“It’s all based on credentials – they even have scan protection against fraudsters who want to sell fake server logins,” he added.
These access credentials are based on the Remote Desktop Protocol (RDP) bundled with Microsoft Windows, which by default is disabled but can be enabled remotely by systems administrators, according to Kamluk.
“What was surprising was the cost to purchase these access credentials was only US$6 to US$15,” he said.
“Imagine the pretty advanced hackers out there hunting for breaches in government, corporate or telco networks – with these services, cybercriminals can spend only up to US$10 to purchase the first launchpad into any country,” he added.
Discovery and depth
 The uncovering of the xDedic marketplace came about after a European ISP approached Kaspersky Lab because its servers were constantly being compromised, according to Kamluk (pic).
The uncovering of the xDedic marketplace came about after a European ISP approached Kaspersky Lab because its servers were constantly being compromised, according to Kamluk (pic).
“Its servers were being compromised again and again; even after clean-ups and other necessary actions, the attackers could still get access back,” he said.
“Our investigation showed the installation of certain tools that referenced the xDedic marketplace, which turned out to be a website where anyone can log in and see the servers on offer,” he added.
After more research, Kaspersky Lab discovered that servers from both developed and emerging markets were part of the xDedic marketplace.
The servers were marked as hosting certain websites or services, including gaming, betting and online banking and payment activities, with some having pre-installed software to facilitate attacks, according to Kaspersky Lab.
“On the website, they show the other side of RDP; they actually explain and teach what you can do once you gain access to the server, including registering accounts in banks, shops’ payment systems, etc., using someone else’s credit card to pay for the goods and deliver them, for example,” said Kamluk.
“Some servers had gambling software, which was probably used to launder money.
“These compromised servers can also be used for sending spam, and hosting trojans, viruses and backdoors.
“They can also be used as proxy servers or as a virtual private network (VPN) to hide your real IP (Internet Protocol) address,” he added.
Such a cybercrime marketplace is not entirely new, and is part of the growing trend of cybercrime- or crimeware-as-a-service.
“Earlier this year, we reported on a malware-as-a-service platform, which creates a backdoor for you that won’t be detected by antiviruses,” said Kamluk.
“It is definitely a developing trend in the criminal world to provide crimeware-as-a-service, a one-stop-shop for young criminals to buy all the ammunition they need to start hacking,” he added.
Prevention and mitigation
The global listing of compromised servers drives home the point that Asia is now emerging as ripe for the picking for cybercriminals.
To minimise exposure, Kamluk suggested strong passwords, among other measures.
“They got into these servers by leveraging on weak passwords on administrator accounts on RDP servers exposed to the Internet; to counter that, users should select complex passwords,” he said.
“You should also consider if you really need RDP servers exposed to the Internet. If you do, because of a business requirement for example, you should whitelist IP addresses that can connect to the server.
“This would eliminate threats from brute-force attackers, as they won’t be able to find it in the first place,” he added.
Then there is the advice too many seem to ignore: Patch your systems and make sure you’re running the latest versions of your server software.
Finally, Kamluk recommends using endpoint protection to counter backdoors planted by attackers.
“These attackers … create a backdoor in your system to ensure even if the account is locked or expired, they can get access back to the server to create a new account. These backdoors can be detected by most antivirus solutions,” he said.
Related Stories:
The day Malaysia painted a bull’s eye on itself
Asia in the crosshairs of APT attackers: FireEye CTO
Zombies are already present in your ATM networks: Kaspersky Lab report
For more technology news and the latest updates, follow us on Twitter, LinkedIn or Like us on Facebook.


