DNS hijacking: Government needs to step in: Page 2 of 2
By Gabey Goh July 5, 2013
 The DNS vulnerability issue
The DNS vulnerability issue
While no valuable data was compromised during this most recent incident, the hijacking of a domain registrar’s servers has highlighted the growing preference of attackers to leverage on DNS vulnerabilities.
In an email interview with DNA, Vic Mankotia, CA Technologies vice president for Security in Asia Pacific & Japan, noted that while the motivations and source behind the hijacking have yet to be determined, "there is no denying" that DNS server attacks are gathering momentum.
“To secure a DNS server, companies need to understand how others might exploit it. The most common threats are Denial of Service (DoS) attacks, tampering with DNS records, and information gathering.
"DoS attacks are probably the most common threat because they’re remarkably easy to pull off, thanks to the large number of incorrectly configured DNS servers on the Internet,” he said.
Mankotia added that one common method of DNS tampering is cache poisoning, in which an attacker injects fake records into a DNS server’s cache.
Other methods of modifying DNS records include forged packets, man-in-the-middle attacks, and rogue DNS servers. In addition to modifying records, attackers use DNS servers for information gathering through DNS server mining, zone transfers, and DNS packet interception.
“Properly configured DNS servers can greatly limit your exposure to all these tactics,” he said.
In a phone interview with DNA, Pavan Joshi, product manager, Web Security Solutions, Asia Pacific & Japan at Akamai Technologies, said that DNS systems are critical infrastructure that often gets overlooked when it comes to security.
“We’re increasingly seeing hackers targeting DNS servers as a means to gain access. It offers a higher return on investment from their point of view, to attack the weak links to get in and DNS is that weak link,” he said.
Pavan said that globally, the company is also seeing an increase in distributed denial-of-service (DDoS) attacks aimed at DNS servers.
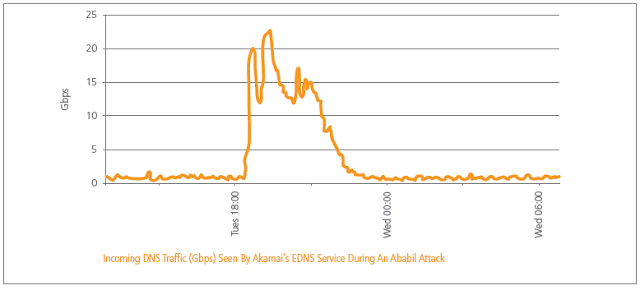 He pointed to the DDoS attacks associated with Operation Ababil that was targeted at American banks and financial institutions. Among those attacks targeting Akamai customers, the company observed up to 65Gbps of total attack traffic, with nearly 23Gbps of attack traffic targeting DNS servers (see chart).
He pointed to the DDoS attacks associated with Operation Ababil that was targeted at American banks and financial institutions. Among those attacks targeting Akamai customers, the company observed up to 65Gbps of total attack traffic, with nearly 23Gbps of attack traffic targeting DNS servers (see chart).
CA Technologies' Mankotia added that DNS servers are often the launching points for DoS attacks, wherein an attacker uses a DNS server that allows recursion to pummel another server with packets.
This kind of attack starves the target server of resources and prevents legitimate users from accessing it. DNS tampering, which takes several forms, is less common but still a threat.
“Whilst these attacks are threat-based and infrastructure security related, companies can also protect themselves by raising the security to the public domains with web access management in the cloud,” he said, pointing to CA Technologies’ own CA CloudMinder solution as one such example.
Akamai's Pavan said that to address the issue of DNS security, there has to be a combination of both public and private sector initiatives. "This affects everyone on the Internet and attacks are now only a question of time and its importance must be realised,” he said.
“The incident in Malaysia is definitely something that would make organisations think about implementing a more robust security solution. Gone are the days when you could have had one or two DNS servers in your data centre and feel safe -- extreme distributed DNS systems must be considered,” he said.
When asked for his opinion on the adoption of Domain Name System Security Extensions (DNSSEC), Pavan said that it would be a good way of mitigating the severity of such DNS attacks.
“DNSSEC should definitely help towards mitigation -- it protects applications from using spoofed DNS records, as all responses from DNSSEC records are digitally signed and authenticated,” he said.
Pavan also pointed out that such implementations should be mandated by governments, in order to establish security benchmarks and compel corporate action.
“The government has to step in at some point to mandate the use of additional security protocols for DNS servers. However, this will take some time as even the United States took about 10 years to do so since the release of DNSSEC,” he said.
In 2008, as part of the US Government's effort to increase its level of service to the public, agencies were instructed to implement DNSSEC measures for all websites in the ‘.gov’ domain.
Pavan noted that in the Asia Pacific region, all markets were currently at the same level in terms of DNS security, with most companies only implementing it if deemed necessary. Such moves have come predominantly from those in the financial services and e-commerce space.
“I don’t think that it would take as long in Asia, we could perhaps see some movement toward such mandates this year,” he added.
Adoption will also take time, noted Pavan, especially on the part of organisations, as there are multiple issues to consider such as the cost implications, the infrastructure changes incurred and the evaluation of return on investment (ROI).
“However in recent months, we have been observing traction and increasing interest for Akamai’s DNS security products from customers. There is increasing understanding that security is an issue that can’t be ignored and companies are making it a part of their overall investment in IT infrastructure,” he said.
Related Stories:
Malaysian sites hit by DNS poisoning
DNS poisoning: MYNIC admits servers compromised
Cyber-war: Time for our agencies to step up
For more technology news and the latest updates, follow @dnewsasia on Twitter or Like us on Facebook.


